BGP: Border Gateway Protocol
Contents
Introduction
This tutorial discusses the plugin bgpDecode.
Preparation
First, restore T2 into a pristine state by removing all unnecessary or older plugins from the plugin folder ~/.tranalyzer/plugins:
t2build -e -y
Are you sure you want to empty the plugin folder '/home/wurst/.tranalyzer/plugins' (y/N)? yes
Plugin folder emptied
Then compile the core (tranalyzer2) and the following plugins:
t2build tranalyzer2 basicFlow bgpDecode txtSink
...
BUILD SUCCESSFUL
If you did not create a separate data and results directory yet, please do it now in another bash window, that facilitates your workflow:
mkdir ~/data ~/results
The sample PCAP used in this tutorial can be downloaded here: test.pcap.
Please save it in your ~/data folder.
Now you are all set for analyzing BGP traffic!
bgpDecode
Let’s look at the plugin configuration first:
bgpDecode
vi src/bgpDecode.h
...
/* ========================================================================== */
/* ------------------------ USER CONFIGURATION FLAGS ------------------------ */
/* ========================================================================== */
#define BGP_DEBUG 0 // activate debug output
#define BGP_IP_FORMAT 1 // 0: hex, 1: IP, 2: int
#define BGP_AS_FORMAT 0 // 0: ASPLAIN, 1: ASDOT, 2: ASDOT+
#define BGP_NOTIF_FORMAT 0 // 0: uint8, 1: string (code only)
#define BGP_TRAD_BOGONS 1 // flag traditional bogons
#define BGP_OUTPUT_RT 1 // output routing tables
#if BGP_OUTPUT_RT == 1
#define BGP_ORIG_ID 0 // output originator id
#define BGP_AGGR 0 // output aggregator
#define BGP_CLUSTER 0 // output cluster list
#define BGP_COMMUNITIES 0 // output communities
#define BGP_MASK_FORMAT 1 // 0: hex, 1: IP, 2: int
#define BGP_AS_PATH_AGGR 0 // aggregate repetitions of the same AS
#endif // BGP_OUTPUT_RT
// Experimental
#define BGP_RT 1 // store routing information in a hashtable (required for MOAS detection)
#define BGP_DEBUG_RT 0 // activate debug output for routing information
#define BGP_RT_MASK 0 // use the mask as part of the key for the routing table
#define BGP_ASIZE 512 // Size of arrays for update records
/* +++++++++++++++++++++ ENV / RUNTIME - conf Variables +++++++++++++++++++++ */
#define BGP_SUFFIX "_bgp.txt"
#define BGP_ANOM_SUFFIX "_bgp_anomalies.txt"
#define BGP_MOAS_SUFFIX "_bgp_moas.txt"
/* ========================================================================== */
/* ------------------------- DO NOT EDIT BELOW HERE ------------------------- */
/* ========================================================================== */
...Run t2 on the supplied pcap.
t2 -r ~/test_data/data/test.pcap -w ~/results/
First, let’s have a look at the aggregated flags!
tawk -V bgpStat=0x8501 -V bgpAFlgs=0x0160 -V bgpPAttr=0x000000ffThe bgpStat column with value 0x8501 is to be interpreted as follows: bit | bgpStat | Description ============================================================================= 0 | 0x0001 | Flow is BGP 8 | 0x0100 | IAT for update or keep-alive < 0 10 | 0x0400 | Atomic Aggregate 15 | 0x8000 | Malformed packet (snaplen) The bgpAFlgs column with value 0x0160 is to be interpreted as follows: bit | bgpAFlgs | Description ============================================================================= 5 | 0x0020 | Multiple Origin AS (same prefix announced by more than one origin AS) 6 | 0x0040 | AS prepended more than 10 times in AS path (average AS path length is between 4 and 5) 8 | 0x0100 | Route for more specific prefix advertised The bgpPAttr column with value 0x000000ff is to be interpreted as follows: bit | bgpPAttr | Description ============================================================================= 0 | 0x0000 0001 | ORIGIN 1 | 0x0000 0002 | AS_PATH 2 | 0x0000 0004 | NEXT_HOP 3 | 0x0000 0008 | MULTI_EXIT_DISC (MED) 4 | 0x0000 0010 | LOCAL_PREF 5 | 0x0000 0020 | ATOMIC_AGGREGATE 6 | 0x0000 0040 | AGGREGATOR 7 | 0x0000 0080 | COMMUNITIES
The absence of the Aggregated bgpCaps line tells us there are no capability flags set.
Second, let’s extract all BGP flows from the flow file:
tawk 'bitsanyset($bgpStat, 0x0001)' ~/results/test_flows.txt | tcol
%dir flowInd flowStat timeFirst timeLast duration numHdrDesc numHdrs hdrDesc srcMac dstMac ethType ethVlanID srcIP srcIPCC srcIPOrg srcPort dstIP dstIPCC dstIPOrg dstPort l4Proto dstPortClassN dstPortClass bgpStat bgpAFlgs bgpMsgT bgpNOpen_Upd_Notif_KeepAl_RteRefr bgpVersion bgpSrcAS_dstAS bgpSrcId_dstId bgpHTime bgpCaps bgpPAttr bgpNAdver bgpNWdrwn bgpMaxAdver bgpAvgAdver bgpMaxWdrwn bgpAvgWdrwn bgpAdvPref bgpWdrnPref bgpNIGP_EGP_INC bgpMinASPLen bgpMaxASPLen bgpAvgASPLen bgpMaxNPrepAS bgpMinIatUp bgpMaxIatUp bgpAvgIatUp bgpMinIatKA bgpMaxIatKA bgpAvgIatKA bgpNotifCode_Subcode
A 1 0x0400000000004000 1408728456.284444 1408728713.990284 257.705840 1 3 eth:ipv4:tcp d4:ca:6d:e4:8f:07 02:e4:64:fc:26:00 0x0800 82.197.169.69 ch "Silvan Gebhardt" 59556 172.16.69.2 05 "Private network" 179 6 179 bgp 0x8501 0x0160 0x14 0_332_0_6_0 0 0_0 0.0.0.0_0.0.0.0 0 0x0000 0x000000ff 470 57 21 1.440727 5 0.171687 0x00fed000 0x00f00000 265_2_61 1 22 5.654655 15 0.000000 20.933496 1.269217 0.000000 54.003614 49.674990 0_0Only one flow!
Let’s now have a look at the different files created by the plugin:
ls ~/results
test_bgp_anomalies.txt test_bgp_moas.txt test_bgp.txt test_flows.txt test_headers.txt
Here is a quick summary of what you’ll find in each file:
- test_bgp.txt: the routing tables (all the routes advertised)
- test_bgp_anomalies.txt: all the anomalies encountered (bogons, blackholes, loops, private/reserved ASN, …)
- test_bgp_moas.txt: all networks with multiple origins AS (MOAS)
In the following sections, we will look into each file and experiment with the supporting scripts!
BGP AS connection file
First, let’s look at the advertised routes:
head ~/results/test_bgp.txt | tcol
%NLRI AS NextHop MED LocPref Origin OriginatorID OriginAS UpstreamAS DestAS Aggregator ASPath ASPathLen MaxNPrepAS ClusterList ClusterListLen Communities WithdrawnRoutes flowIndex Packet Record Timestamp
103.31.109.0/24 0 213.144.128.177 1 100 INCOMPLETE 0.0.0.0 45786 4761 13030 0:0.0.0.0 13030;7473;4761;45786 4 0 0 13030:1;13030:1022;13030:7212;13030:51902 185.56.88.0/22 1 2 1 1408728457.838732
200.16.16.0/20 0 213.144.128.177 1 100 INCOMPLETE 0.0.0.0 27790 3597 13030 0:0.0.0.0 13030;3257;18747;11014;3597;27790 12 6 0 3257:4000;3257:8126;3257:50002;3257:50120;3257:51100;3257:51103;13030:1;13030:3257;13030:7173;13030:51203 1 3 1 1408728457.851349
202.70.64.0/21;202.70.88.0/21 0 213.144.128.177 1 100 IGP 0.0.0.0 23752 6453 13030 0:0.0.0.0 13030;2828;6453;23752 4 0 0 13030:2;13030:2828;13030:7215;13030:51903 1 3 2 1408728457.851349
165.98.159.0/24 0 213.144.128.177 1 100 IGP 0.0.0.0 27742 23520 13030 27742:250.160.35.200 13030;23520;27742 3 0 0 13030:1;13030:1021;13030:7167;13030:51901;23520:10000;23520:10040 1 3 3 1408728457.851349
194.31.36.0/23;194.31.38.0/24 0 213.144.128.177 1 100 IGP 0.0.0.0 198431 50481 13030 198431:1.36.31.194 13030;3549;3356;50481;198431 5 0 0 3549:2722;3549:31276;13030:2;13030:3549;13030:7179;13030:51202 1 3 4 1408728457.851349
165.98.12.0/22;190.124.38.0/24 0 213.144.128.177 1 100 IGP 0.0.0.0 27742 23520 13030 0:0.0.0.0 13030;3257;23520;27742 4 0 0 3257:4000;3257:8126;3257:50002;3257:50120;3257:51100;3257:51103;13030:1;13030:3257;13030:7173;13030:51203 1 3 5 1408728457.851349
195.54.176.0/23 0 213.144.128.177 1 100 IGP 0.0.0.0 51147 28917 13030 0:0.0.0.0 13030;3549;174;28917;51147 5 0 0 3549:2352;3549:30840;13030:2;13030:3549;13030:7214;13030:51701 1 3 6 1408728457.851349
185.47.232.0/22 0 213.144.128.177 1 100 IGP 0.0.0.0 16024 3209 13030 0:0.0.0.0 13030;3209;16024 5 2 0 13030:1;13030:1017;13030:4005;13030:7179;13030:51000;13030:51202 1 3 7 1408728457.851349
64.29.130.0/24 0 213.144.128.177 1 100 IGP 0.0.0.0 23342 4436 13030 0:0.0.0.0 13030;3549;2914;4436;23342 6 1 0 2914:410;2914:1002;2914:2000;2914:3000;3549:2714;3549:31276;13030:2;13030:3549;13030:7179;13030:51202 1 3 8 1408728457.851349Let’s look into the supporting scripts to see what we can do with this file!
bgpDecode
cd scripts
ls
asn2cn asn2cn.txt asn.txt bgp2ng bgpMOAScn bgpR
Let’s start with the bgpR script!
./bgpR -h
Usage:
bgpR [OPTION...] file_bgp.txt
Optional arguments:
-t keep the timestamp
-p generate the plots
-d directed graph
-s max one edge between nodes
-u no links to self node
-l label edges with the flowIndex
-n color nodes
-e color edges
-f FMT output format (gif, png, ps, svg, svgz) [default: 'png']
-o DIR output folder [default: '.']
-y do not ask for confirmation before executing an action
-h, --help Show this help, then exitGenerating '/home/wurst/results/test_bgp_s.txt'... OK Sorting '/home/wurst/results/test_bgp_s.txt'... OK Generating '/home/wurst/results/test_bgp_mpath.txt'... OK Generating '/home/wurst/results/test_bgp_conf.txt'... OK Generating 'as' plot... OK Generating 'cn' plot... OK Generating 'cont' plot... OKls ~/results
test_bgp_anomalies.txt test_bgp_as.png test_bgp_cn.png test_bgp_cont.dot test_bgp_moas.txt test_bgp_s.txt test_flows.txt
test_bgp_as.dot test_bgp_cn.dot test_bgp_conf.txt test_bgp_cont.png test_bgp_mpath.txt test_bgp.txt test_headers.txt
Plenty of new files! Let’s start by looking at the pictures!
First, we have the connections between AS in ~/results/test_bgp_as.png
feh ~/results/test_bgp_as.png
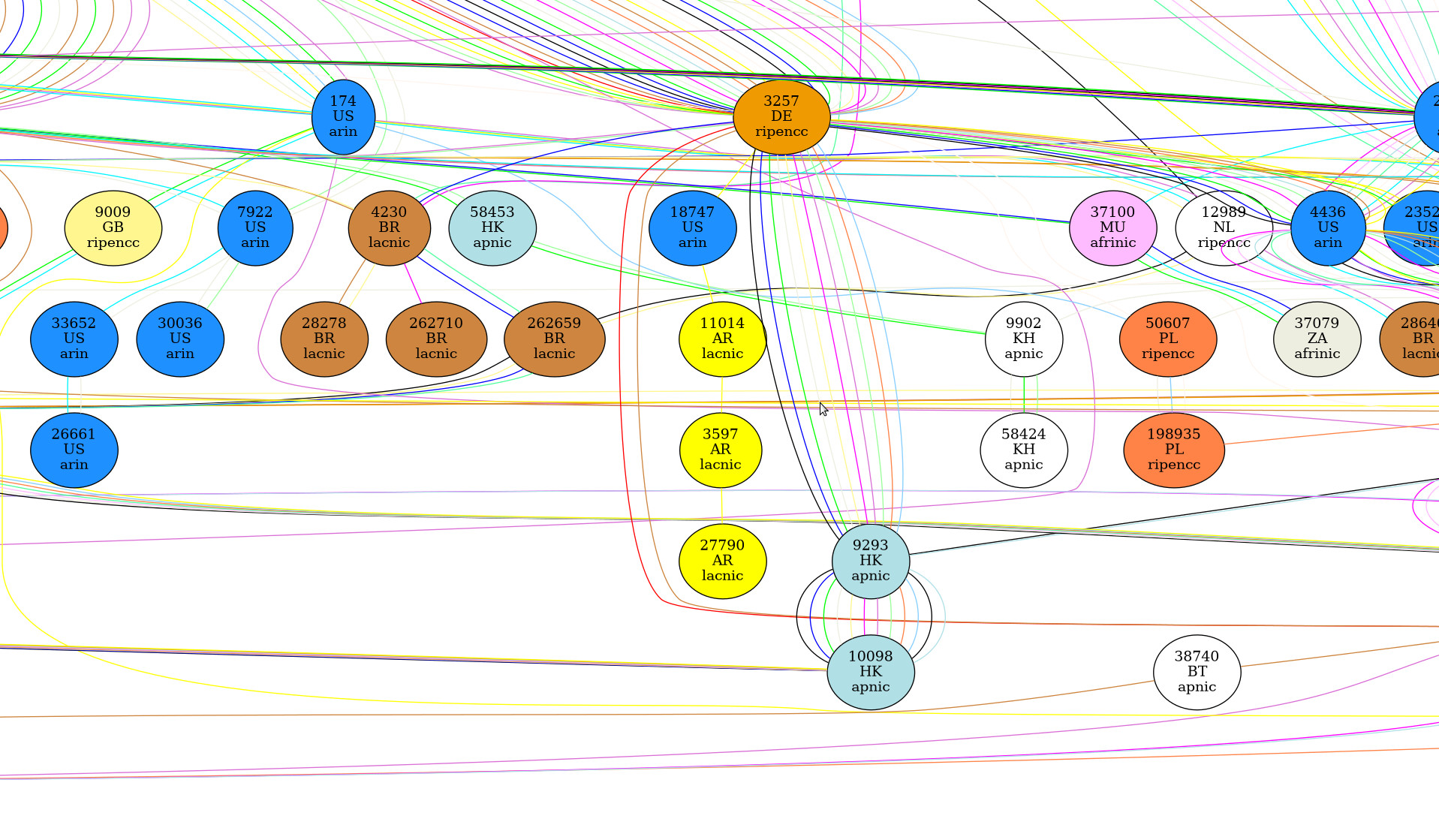
Looks quite messy!
Let’s start again with the -s option to only have one link between nodes!
This time, we’ll look into the connections between countries!
Generating '/home/wurst/results/test_bgp_s.txt'... OK Sorting '/home/wurst/results/test_bgp_s.txt'... OK Generating '/home/wurst/results/test_bgp_mpath.txt'... OK Generating '/home/wurst/results/test_bgp_conf.txt'... OK Generating 'as' plot... OK Generating 'cn' plot... OK Generating 'cont' plot... OK
feh ~/results/test_bgp_cn.png
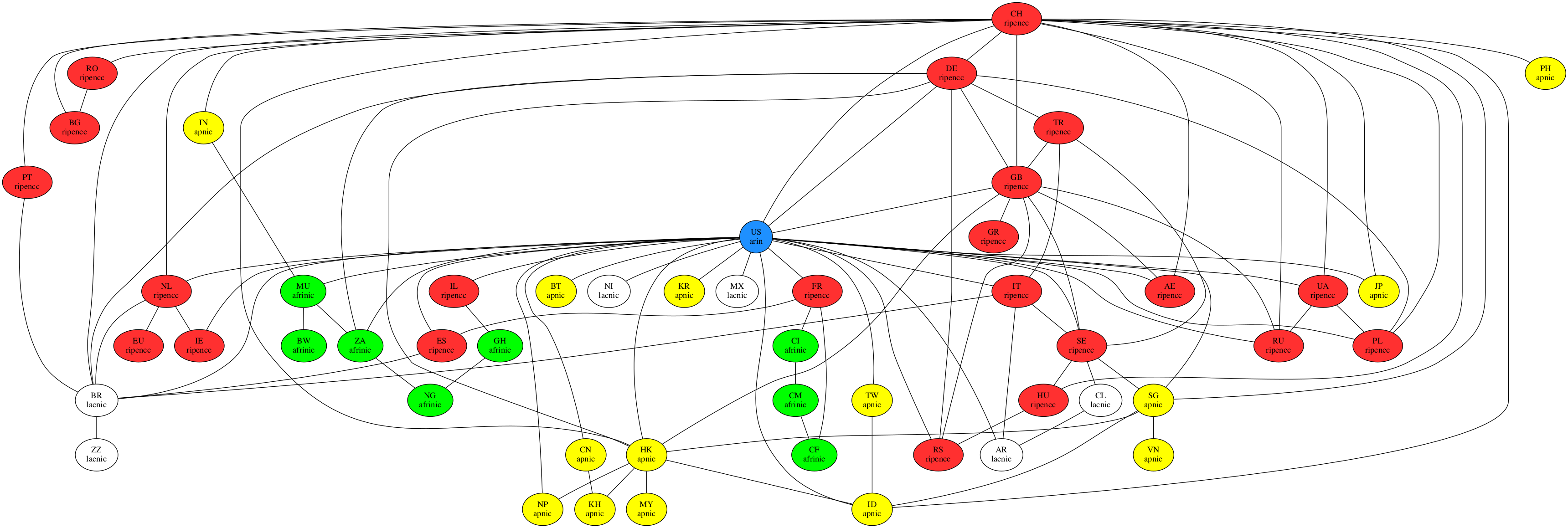
Just to be thorough, let’s have a look at the connections between continents:
feh ~/results/test_bgp_cn.png
For a more precise idea of the continents, refer to the documentation of the plugin:
t2doc bgpDecode

What are the other files?
test_bgp_s.txt: the file used to generate the previous pictures (based on test_bgp.txt, but with one network per line) test_bgp_mpath.txt: all networks with more than one path test_bgp_conf.txt: possible configuration errors (AS prepended N times, followed by AS number N)
The test_bgp_conf.txt file is empty, so let’s look into the test_bgp_mpath.txt file! It reports the number of distinct paths for all networks which have more than one path:
tcol ~/results/test_bgp_mpath.txt
%Network NumberOfDifferentPaths MinPathLen MaxPathLen RangePathLen MeanPathLen MedianPathLen StdDevPathLen ModePathLen MOAS
2.93.180.0/24 7 3 7 4 5.28571 5 1.25357 7
202.70.88.0/21 7 3 9 6 5.42857 6 2.0702 9
103.31.109.0/24 7 3 6 3 5.28571 4.5 1.25357 6
2.93.1.0/24 6 5 7 2 6 6 0.894427 7
2.93.97.0/24 5 5 7 2 6 6 1 7
2.93.146.0/24 5 5 7 2 6 6 1 7
202.70.64.0/21 5 3 7 4 4.8 5 1.64317 7
188.75.52.0/22 5 4 7 3 5.6 5.5 1.34164 7
179.191.0.0/21 5 5 7 2 5.8 6 0.83666 7
176.221.72.0/21 5 5 18 13 10.8 11.5 4.91935 18
128.73.165.0/24 5 5 10 5 7.6 7.5 2.30217 10
185.56.88.0/22 4 4 6 2 5.25 5 0.957427 6
185.22.144.0/22 4 5 10 5 7.5 7.5 2.38048 10
176.15.113.0/24 4 5 7 2 6.25 6 0.957427 7
41.154.231.0/24 3 4 5 1 4.66667 4.5 0.57735 5
41.154.230.0/24 3 4 5 1 4.66667 4.5 0.57735 5
41.154.229.0/24 3 4 5 1 4.66667 4.5 0.57735 5
41.154.228.0/24 3 4 5 1 4.66667 4.5 0.57735 5
2.93.28.0/24 3 5 7 2 6 6 1 7
202.123.88.0/24 3 4 7 3 5.66667 5.5 1.52753 7
195.54.176.0/23 3 3 5 2 4.33333 4 1.1547 5Ok, time to look into the test_bgp_anomalies.txt file!
BGP anomaly file
The test_bgp_anomalies.txt file contains a list of anomalies. Refer to the table below to extract a specific anomaly:
| Bogons advertisement: | awk '/^BOGON/' test_bgp_anomalies.txt |
| Prefix more specific than /24: | awk '/^SPEC24/' test_bgp_anomalies.txt |
| Prefix less specific than /8: | awk '/^SPEC8/' test_bgp_anomalies.txt |
| Possible blackhole: | awk '/^BLACKHOLE/' test_bgp_anomalies.txt |
| Possible loop: | awk '/^LOOP/' test_bgp_anomalies.txt |
| AS number prepended more than 10 times in AS path: | awk '/^NPREPAS/' test_bgp_anomalies.txt |
| Private/Reserved AS numbers: | awk '/^PRIVAS/' test_bgp_anomalies.txt |
| More specific prefix to existing network | awk '/^MSPEC/' test_bgp_anomalies.txt |
| Multiple Origin AS (MOAS) | Reported in test_bgp_moas.txt, discussed in the next section |
Let’s peek into the test_bgp_anomalies.txt file to see how it looks:
tcol ~/results/test_bgp_anomalies.txt
%Anomaly flowInd PktNum RecNum ASorNet RepsOrMask NewMask
MSPEC 1 68 3 177.12.200.0 22 24
MSPEC 1 115 1 179.191.0.0 21 22
MSPEC 1 191 3 179.191.0.0 21 22
MSPEC 1 214 5 187.111.32.0 20 21
NPREPAS 1 215 2 9121 15
MSPEC 1 238 4 176.111.120.0 21 22BGP networks with multiple origins AS (MOAS)
Networks with multiple origins AS (MOAS) are reported in the test_bgp_moas.txt file. Let’s look into it!
tcol ~/results/test_bgp_moas.txt
%Network Mask OldOrigAS NewOrigAS flowInd PktNum RecNum
112.215.16.0 24 17885 24203 1 169 7This tells us that the network 112.215.16.0/24 was advertised first by AS 17885 and later by AS 24203.
Would it not be nice to know which countries those AS operate in?
Let’s try the bgpMOAScn script:
Generating '/home/wurst/results/test_bgp_moas_cn.txt'... OK
Let’s look at the new file!
tcol ~/results/test_bgp_moas_cn.txt
%Network Mask OldOrigAS NewOrigAS OldCountry NewCountry flowInd PktNum RecNum
112.215.16.0 24 17885 24203 ID ID 1 169 7Nice, the country of the AS was added! We can now see that both AS originate from the same country, namely Indonesia.
Conclusion
Don’t forget to reset the plugin configuration for the next tutorial.
t2conf bgpDecode --reset && t2build bgpDecode
Have fun analyzing!